728x90
AWS Certified Developer Associate 자격증을 준비하면서, 알게된 내용을 정리하였습니다. ( + 영어 문서 익숙해지기)
강의(적극 추천드립니다): https://www.udemy.com/course/aws-certified-developer-associate-dva-c01/
AWS Identity & Access Management(AWS IAM)
IAM: Users & Groups
- IAM = Identity and Access Management, Global service
- Root accun는 기본으로 생성되고, 공유하지 않습니다.
- Users are people within your organizations, and can be grouped
사용자는 조직 내의 사용자이며 그룹화할 수 있습니다 - Groups only contain users, not other groups
그롭에는 사용자만 포함되며 다른 그룹은 포함되지 않습니다 - Users don't have to belong to a group, and user can belong to multiple groups
사용자는 그룹에 속할 필요가 없으며 사용자는 여러 그룹에 속할 수 있습니다

IAM: Permissions

- Users or Groups can be assigned JSON documents called policies
- These policies define the permissions of the users
- In AWS you apply the least privilege principle:don't give more permissions than a user need
(AWS에서 최소 권한 원칙을 적용합니다. 사용자가 필요로 하는 것보다 더 많은 권한을 부여하지 마십시오)
IAM Policies inheritance

IAM Policies Structure
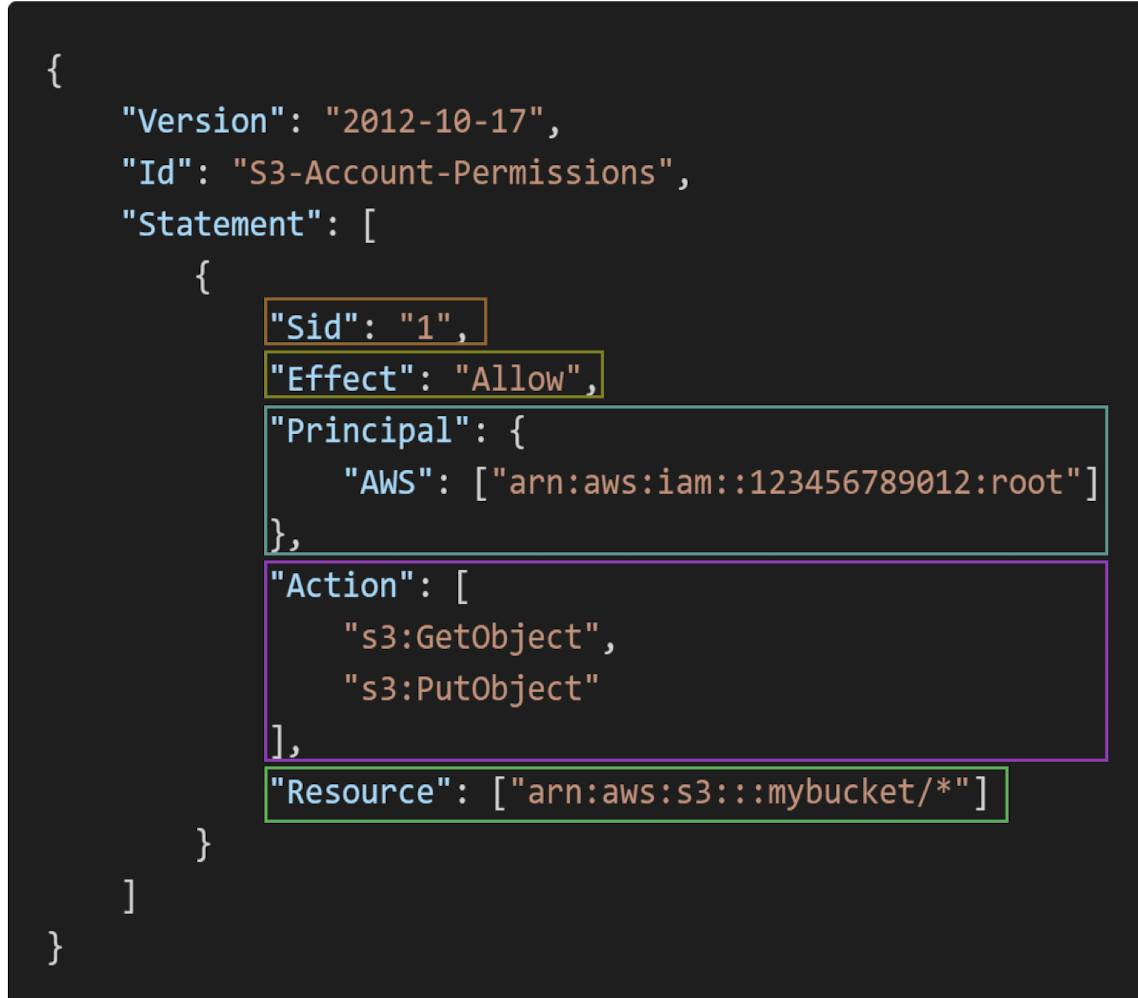
- Consists of
- Version: policy language version, always include "2012-10-17"
- Id: an identifier for the policy (optional)
- Statement: one or more individual statements (required)
- Statements consists of
- Sid: an identifier for the statement (optional)
- Effect: whether the statement allows or denies access (Allow, Deny)
- Principal: account/user/role to which this policy applied to
- Action: list of actions this policy allows or denies
- Condition: conditions foe when this policy is in effect (optional)
IAM - Password Policy
- Strong passwords = higher security for your account
- In AWS, you can setup a password policy:
- Set a minimum password length
- Require specific character types:
- including uppercase letters
- lowercase letters
- numbers
- non-alphanumeric characters
- Allow all IAM users to change their own passwords
- Require users to change their password affter some time (password expiration)
- Prevent password re-use
Multi Factor Authentications - MFA
- Users have access to your account and can possibly change configurations or delete resources in your AWS account.
사용자는 계정에 액세스할 수 있으며 AWS 계정에서 구성을 변경하거나 리소스를 삭제할 수 있습니다 - You want to protect your Root Accounts and IAM users
- MFA = password you know + security device you own
- Main benefit of MFA
- MFA = password you know + security device you own
if a password is stolen or hacked, the account is not compromised

MFA devices options in AWS
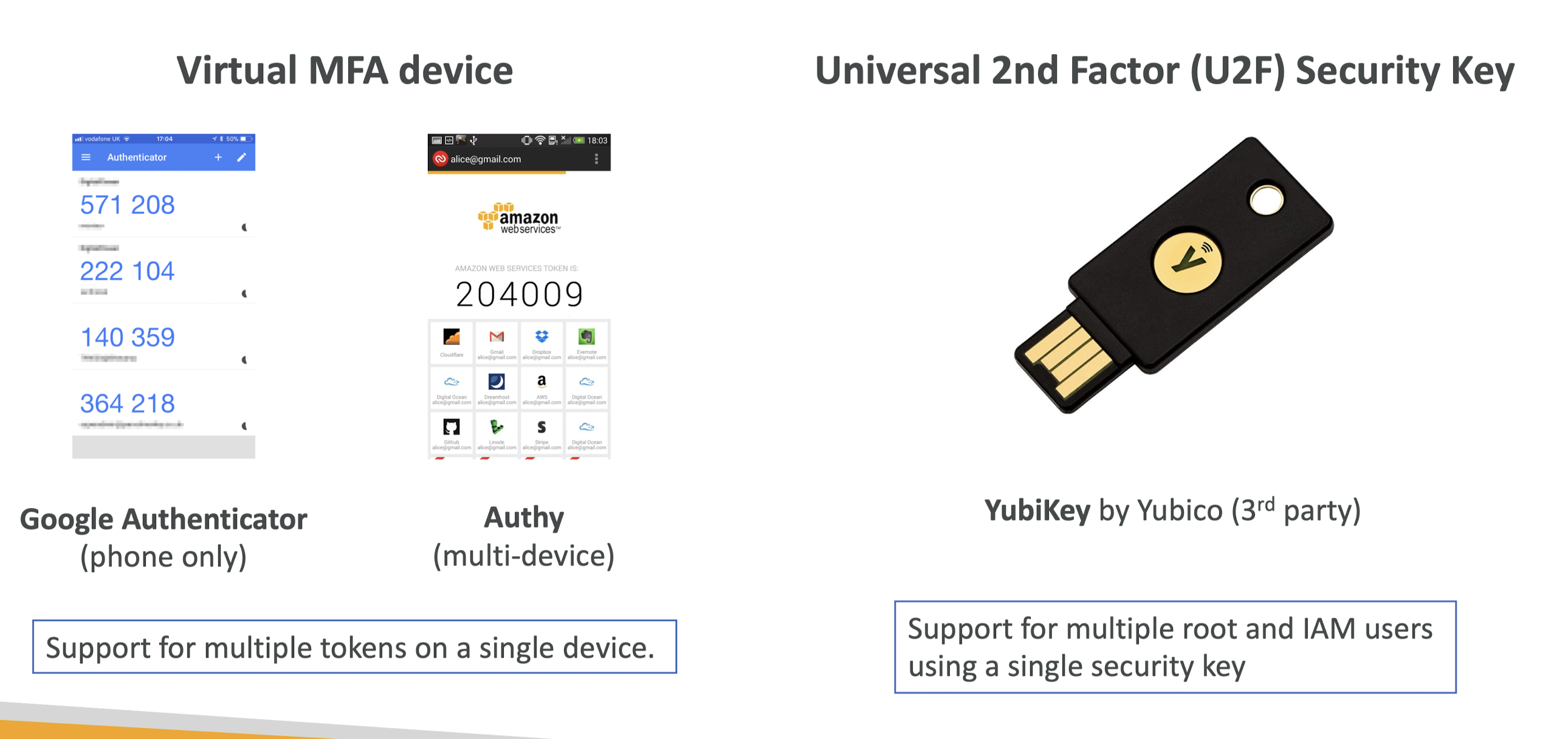
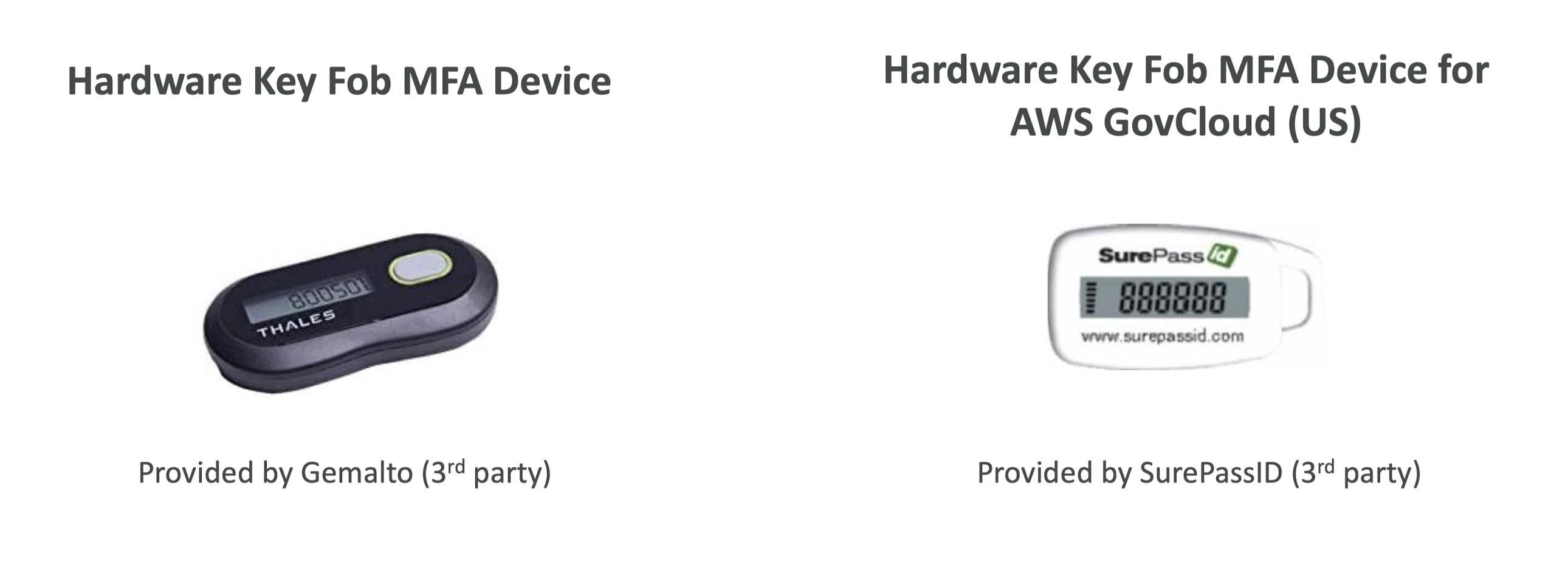
How can users access AWS?
- To access AWS, you have three options:
- AWS Management Console (protected by password + MFA)
- AWS Command Line Interface (CLI): protect by access keys
- AWS Software Developer kit (SDK) - for code:protected by access keys
- Access Keys are generated through the AWS Console
- Users manage their own access keys
- Access Keys are secret, just like a password. Don't share them
- Access key ID ~= username
- secret Access key ~= password
IAM Roles for Services
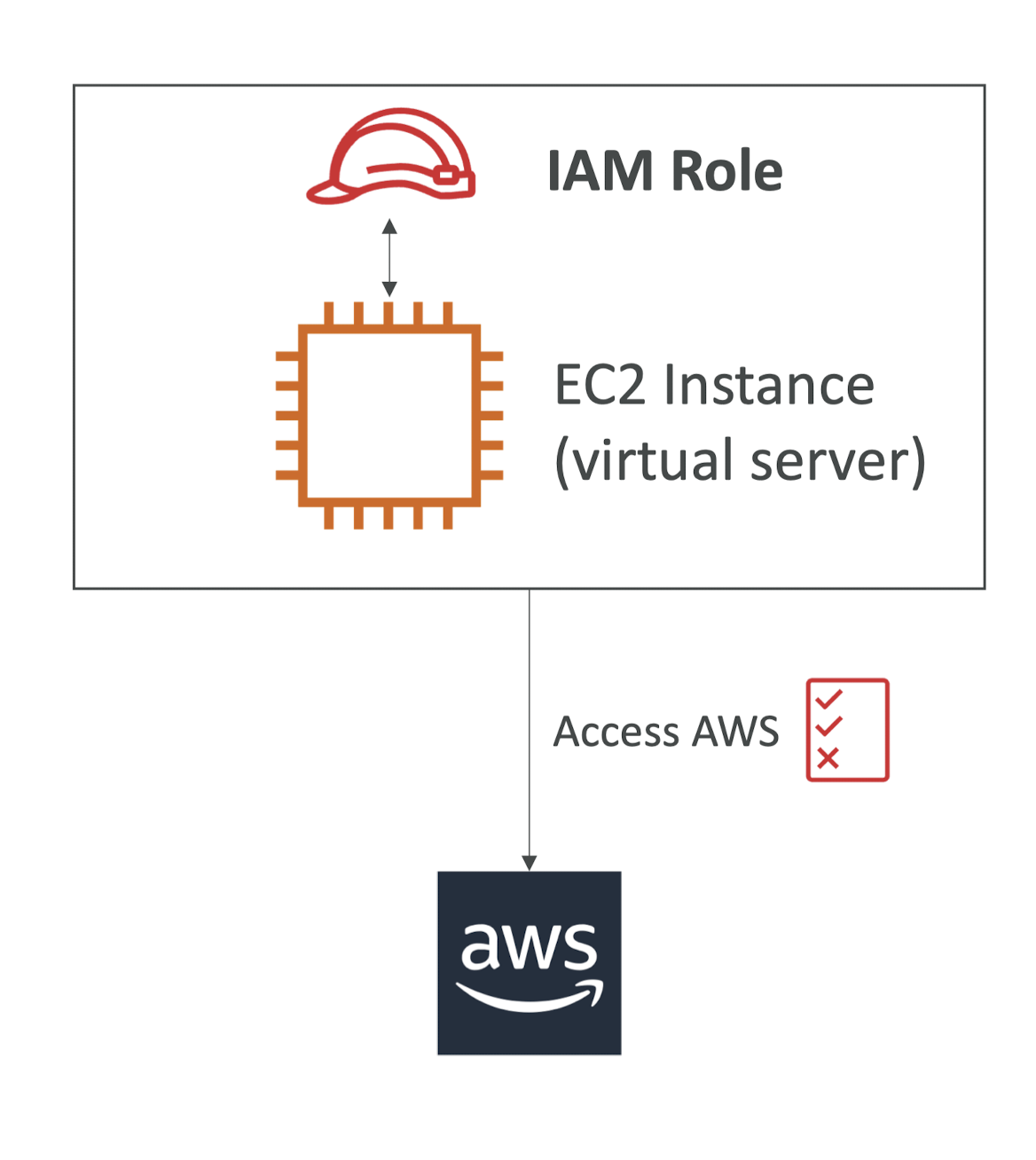
- Some AWS service will need to perform actions on your behalf
일부 AWS 서비스는 사용자를 대신하여 작업을 수행해야 합니다 - To do so, we will assign permission to AWS services with IAM Roles
- Common roles:
- EC2 Instance Roles
- Lambda Funcion Roles
- Roles for CloudFormation
IAM Security Tools
- IAM Credentials Report (accunt-level)
- a report that lists all your account's users and the status of their various credentials
귀하의 계정의 모든 사용자와 다양한 자격 증명의 상태를 나열하는 보고서
- a report that lists all your account's users and the status of their various credentials
- IAM Access Advisor (user-level)
- Access advisor shows the service permissions granted to a user and when those services were last accessed.
액세스 어드바이저는 사용자에게 부여된 이러한 서비스 권한과 해당 서비스가 마지막으로 액세스된 시점을 표시합니다. - You can use this information to revise your policies.
이 정보를 사용하여 정책을 수정할 수 있습니다.
- Access advisor shows the service permissions granted to a user and when those services were last accessed.
IAM Guidelines & Best Practices
- Don't use the root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assign permissions to groups
- Create a strong password policy
- Use and enforce the use of Multi Factor Authentication (MFA)
- Create an use Roles for giving permissions to AWS services
AWS 서비스 사용 권한을 부여하기 위한 역할 생성 - Use Access Keys for Programmatic Access (CLI/SDK)
- Audit permissions of your account using IAM Credentials Report & IAM Access Advisor
- Never share IAM users & Access Keys
Shared Responsibilty Model for IAM
AWS
- Infrastructure (global network security)
- Configuration and vulnerability analysis
- Compliance validation
User (유저가 적용할 점)
- Users, Groups, Roles, Policies management and monitoring
- Enable MFA on all accounts
- Rotate all your keys often
- Use IAM tools to apply appropriate permissions
- Analyze access patterns & review permssions
IAM Section - Summary
- Users: mapped to a physical user, has a password for AWS Console
- Groups: contains users only
- Policies: JSON document that outlines permissions for users or groups
- Roles: for EC2 instances of AWS services
- Security: MFA + Password Policy
- AWS CLI: manage your AWS services using the command-line
- AWS SDK: magage your-AWS services using a programming language
- Access Keys: access AWS using the CLI or SDK
- Audit: IAM Credential Reports & IAM Access Advisor
728x90
'AWS' 카테고리의 다른 글
| AWS Certified Developer Associate 자격증 준비 - Amazon VPC (0) | 2024.01.05 |
|---|---|
| AWS Certified Developer Associate 자격증 준비 - Amazon Route53 (2) | 2024.01.05 |
| AWS Certified Developer Associate 자격증 준비 - RDS,Aurora & ElastiCache편 (1) | 2024.01.04 |
| AWS Certified Developer Associate 자격증 준비 - High Availability & Scalability편 (0) | 2024.01.03 |
| AWS Certified Developer Associate 자격증 준비 - EC2편 (0) | 2024.01.02 |




댓글